Cybersecurity Testing - Known Vulnerabilities Scan - Bureau Veritas P-Scan
P-SCAN is a Vulnerability Scanning service allowing you to validate whether there are any common known vulnerabilities within your IoT product
Bureau Veritas' P-Scan Vulnerability ASSESSMENT
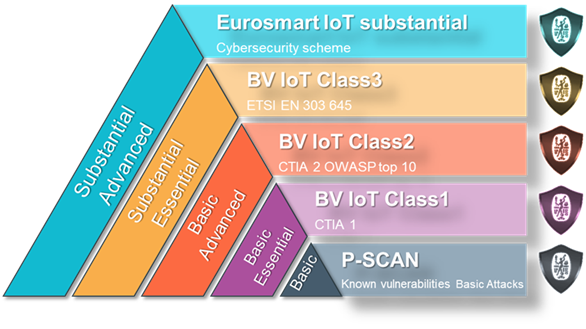
Protection against exploitation of faults and known vulnerabilities is one of the minimal requirements to understand for IoT device manufacturers and is a base requirements in many different regulations.
Bureau Veritas' P-SCAN checks IoT devices in a BlackBox approach against the key known vulnerabilities used by hackers. This is the entry level service within Bureau Veritas' cybersecurity testing suite.
P-SCAN provides an immediate feedback on the communication channel vulnerabilities that are present on the device an can be used by attackers.
Bureau Veritas developed a specific Tool to check the vulnerabilities on the following communication channels:
- Wifi
- Bluetooth Low Energy
- Zigbee
If the device has a web interface the vulnerability scanning is completed using Nessus to check the TCP/IP services vulnerabilities.
P-Scan Service Introduction
Download DocumentAccess Bureau Verias' Cybersecurity Essentials Webinar Series for Free
Register Here for Instant Access
Penetration testing*
For manufacturers who wants to go deeper and check the resistance to attack of their product we offer a penetration testing service based on the latest techniques:
- Hardware Analysis & Assessment
- IoT device reverse engineering
- IoT device disassembling
- Mapping out components and uncovering known and unknown vulnerabilities
- Software Analysis & Assessment
- Firmware, Applications & OS Analysis (provided by the customer or extracted when possible from the device directly)
- Encryption analysis and Obfuscation techniques in use
- Reverse engineering firmware binaries
- 3rd party libraries and SDKs
- Debugging binaries to gain sensitive info
- Mobile application verification
- Attack and Exploitation
*This service is adjusted together with the customer